A No-Nonsense Guide To WordPress Security: Doing The Things That Matter

If you’re like most WordPress users, getting your WordPress site hacked ranks pretty high up there on your list of “nightmare scenarios”.
You might’ve seen those scary posts about hundreds of thousands of WordPress sites getting hacked and…yeesh – is that going to happen to your site?
No! At least not if you take a little time to implement the basics of WordPress security.
WordPress security isn’t some developer-only thing, either. While it certainly can get complex for mission-critical WordPress sites handling sensitive data, for most publications, WordPress security is more about following a set of best practices than typing away like a counter-hacker in a TV show.
In this post, we’re going to demystify the topic with a WordPress security plan that will benefit all types of WordPress sites, from big publications all the way down to solo bloggers.
#The Million Dollar Question: Is WordPress Secure?
Before we can tell you how to secure your WordPress site, we need to spend a little time telling you how WordPress sites get hacked in the first place so that you know what you’re up against.
While it’s hard to come up with exact numbers, it’s safe to say that hundreds of thousands of WordPress sites get hacked every year at a minimum.
And that number certainly sounds scary…until you remember that WordPress powers over 31% of the entire Internet.
Because of their popularity, the raw number of WordPress sites that get hacked every year is always going to be high and WordPress is, unfortunately, quite a juicy target for hackers.
So is WordPress secure? And if it is secure (spoiler – it is), how are hundreds of thousands of WordPress sites still getting hacked?
The answer requires some nuance…
See, there’s a difference between the core WordPress software and how people use WordPress in real life.
If you took the core WordPress software, put it on a secure host, and kept it updated, we can almost guarantee it would never experience any issues.
But most sites don’t operate in that idyllic scenario, and here’s when security vulnerabilities get introduced:
- If you don’t keep everything updated, especially when it comes to security patches
- When you use themes and plugins that might not be as secure as the core WordPress software
- When you use a weak password and don’t secure your login area.
#Here’s What The Data Says About How WordPress Sites Get Hacked
To support the list above, here’s what the data actually says about how WordPress sites get hacked.
First off, Sucuri publishes regular hacked website reports which demonstrate a clear correlation between out-of-date WordPress software and hacked websites:
- 39.3% of the hacked WordPress sites in Sucuri’s 2017 report were out of date.
- 55% of the hacked WordPress sites in Sucuri’s Q2 2016 report were out of date
- 61% of the hacked WordPress sites in Sucuri’s Q3 2016 report were out of date.
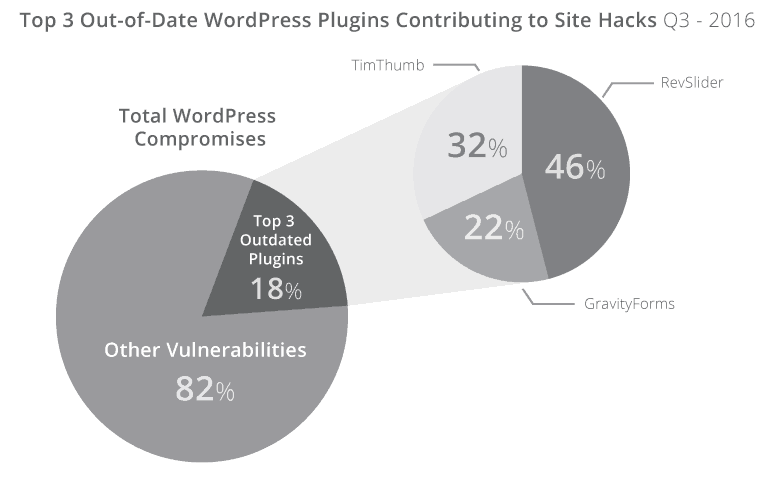
What’s more, 18% of the hacked WordPress sites that Sucuri looked at in Q3 2016 were compromised because of out-of-date versions of just 3 popular plugins:
Right off the bat, you should notice a pretty strong correlation between un-updated WordPress software and hacked sites.
And this makes sense – if you head to the WPVulnDB, a directory of known WordPress vulnerabilities, you’ll see that the vast majority of exploits involve past versions of WordPress:
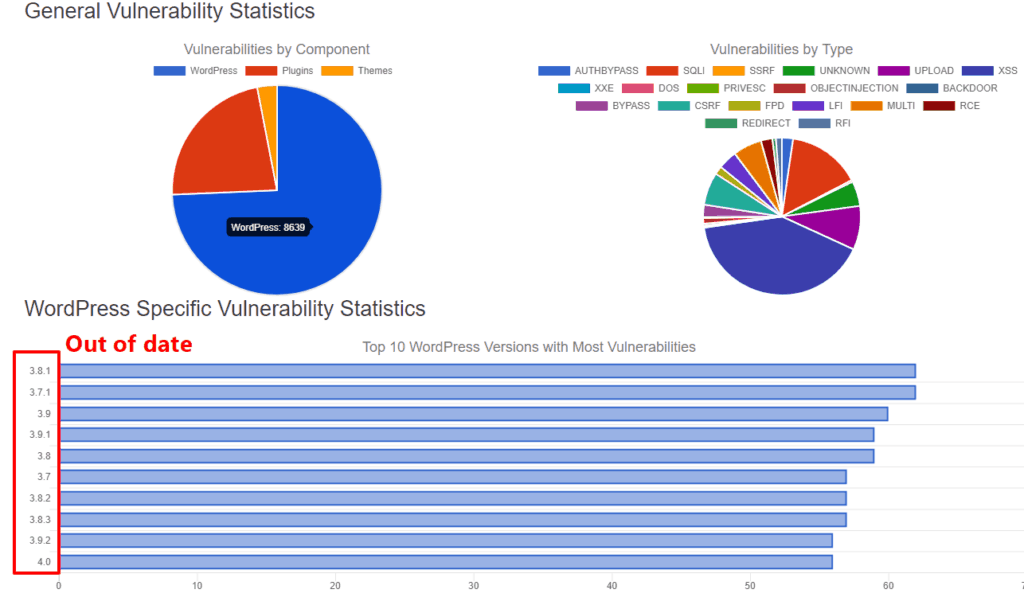
It’s not just out of date software that causes hacks, though.
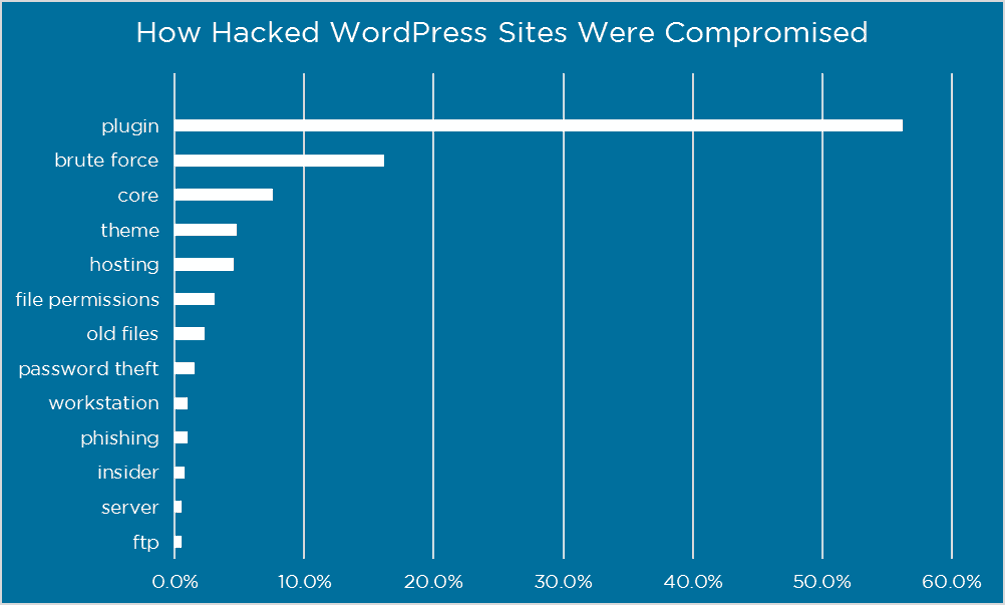
In 2016, Wordfence surveyed 1,032 people with hacked WordPress sites to see how their site got hacked.
Of the people who knew how their site got hacked (which was only ~31.5% of respondents), here’s how hackers got in:
- Plugin and theme vulnerabilities accounted for ~60% of the attacks
- Compromised login credentials accounted for ~20% of the attacks
At this point, you should see how the data leads to that list we shared above.
Most WordPress sites get hacked because of:
- Out-of-date software
- Vulnerabilities in third-party extensions
- Weak account security.
So, if you want to keep your WordPress site secure, your top focus should be on preventing those three issues.
#The Five Biggest Things You Can Do To Secure Your WordPress Site Right Now
As in much of life, the Pareto principle is a good way for most people to approach WordPress security. Also known as the 80/20 rule, the basic idea is that 80% of your results come from 20% of your efforts.
What that means for WordPress security is that there are a few basic principles you can implement to cover most security issues on your site.
If you take nothing else from this post, you should absolutely implement these tips.
Later on, we’ll share some additional smaller security tips that can address some of the rarer ways in which WordPress sites get hacked. Those tips are still beneficial, but their effects aren’t as large.
Note – to implement these tips, we’ll provide standalone plugin solutions where needed. But the Wordfence plugin can also implement many of these tips for you, and we’ll let you know when that’s the case.
#1. Keep WordPress Updated (Always)
You need to keep your WordPress site updated if you want it to stay secure (remember the data!). This includes both the core software, as well as your themes and plugins.
#An Example Of Why Prompt WordPress Updates Matter
In February 2017, hundreds of thousands of WordPress sites were defaced due to a REST API vulnerability in the WordPress core.
But a week prior to the vulnerability being exploited, the WordPress core team released WordPress 4.7.2 to fix the issue. All the sites that promptly updated to WordPress 4.7.2 were 100% safe.
And here’s something important to know:
Similar issues will keep happening because the WordPress Security team has a policy of Responsible Disclosure. Basically, this means that the core team publicly releases known vulnerabilities once they’ve been patched.
So with the REST API vulnerability example from above, it went like this:
- The WordPress security team became aware of the vulnerability.
- While the vulnerability was still private, the Security Team quietly patched it and released the fix in WordPress 4.7.2
- After a one-week delay to give people time to update, the Security Team publicly disclosed the vulnerability in accordance with their Responsible Disclosure policy.
- Once it became known, malicious actors started exploiting the vulnerability, which affected WordPress sites that hadn’t updated.
Basically – this stuff isn’t just theory. You’ll see the same scenario play itself out every time a new vulnerability is discovered. If you want to make sure your site doesn’t become a victim, all you need to do is keep it updated.
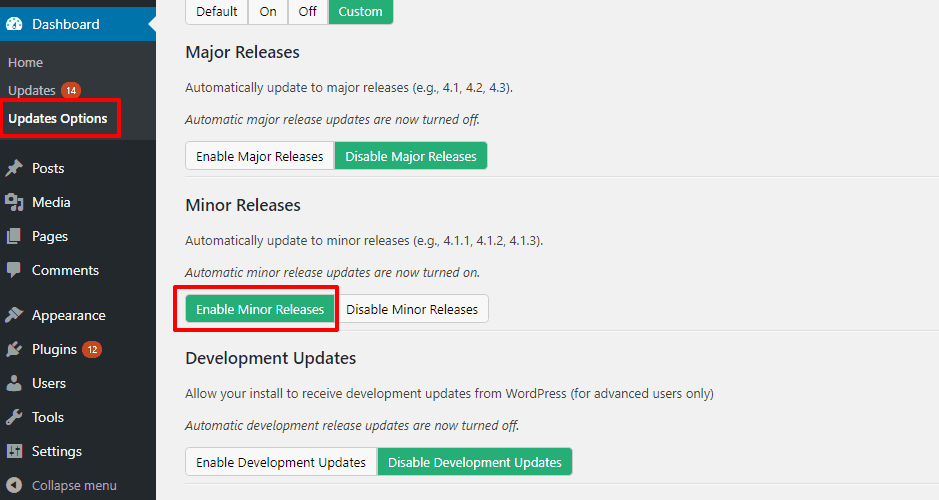
#Make Sure Automatic Updates Are Turned On For Security Releases
By default, all WordPress sites have automatic updates turned on for minor security releases.
As long as you or your host doesn’t turn this feature off, your WordPress core should always be secure.
If you’re not sure whether or not you have automatic security updates enabled, you can use the free Easy Updates Manager plugin to check:
Or, if you’d prefer to do things manually, you can add the following line to your wp-config.php:
define( 'WP_AUTO_UPDATE_CORE', minor );This will ensure that your site automatically applies security updates. But it won’t automatically apply non-security major updates (e.g. WordPress 5.0).
#Set Up Email Notifications For Plugin/Theme Updates
The Easy Updates Manager plugin above also lets you enable automatic updates for your theme and plugins.
While this is one way to make sure you’re always running the latest versions, it’s not a great choice for most sites because there’s always a chance that a new plugin or theme update causes compatibility issues on your site. And with automatic updates, you might not be around to fix the issue.
With that being said, you still want to make sure that you’re able to promptly update all your extensions, so there’s a good middle-ground:
If you can’t check in to your WordPress dashboard on a regular basis, use the free WP Updates Notifier plugin to receive email notifications whenever a new plugin or theme update is available:
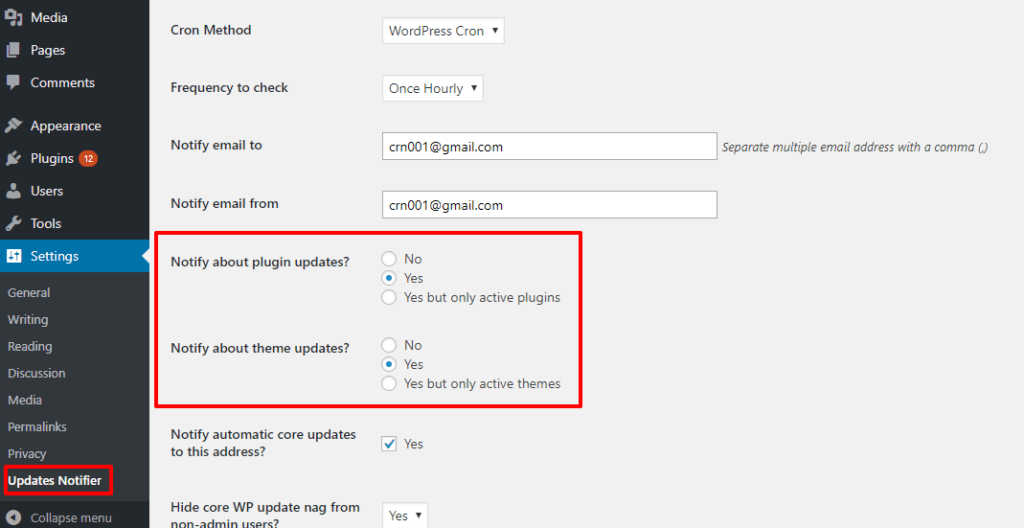
That way, you’ll know that you need to manually hop on your site and oversee the update.
#2. Choose A Secure WordPress Host
Because your host is your site’s foundation, it plays a big role in keeping your WordPress site secure.
There are a few things that make a secure host.
First, it should give you access to the latest secure technologies to access and power your site, including:
- SFTP – unlike regular FTP, this encrypts your FTP login credentials to keep them safe.
- PHP 7.X – older versions of PHP 5.x have reached their end of life and no longer receive security updates. Your host must offer the latest versions.
- SSL certificates – ideally, a free SSL/TLS certificate from Let’s Encrypt (or another free provider).
Beyond that, a secure host will put proactive measures in place to stop security issues before they happen. These protections should include web application firewalls, as well as WordPress-specific server configurations to promote security.
For example, at Presslabs we implement the following security configurations:
- Block arbitrary PHP execution
- wp-admin security with HTTPS and Perfect Forward Secrecy
- The separation between your public site and wp-admin area
- Proper file permissions
- Restricted database access.
#3. Follow Best Practices For Plugins And Themes
Beyond keeping your theme and plugins updated, you also need to make sure that you’re following other good practices for extensions
Remember, in that Wordfence survey, ~60% of people’s sites got hacked because of their theme or plugins, so this is a major attack vector.
In addition to keeping everything updated, here are some other best practices to follow:
#Be Careful About Which Extensions You Use
While bad things can happen to good extensions, you can give your site the best chance possible by only installing high-quality plugins and themes in the first place.
Here are some good rules to follow:
- Use reputable developers/marketplaces – stick to marketplaces like WordPress.org or Envato, or trusted third-party developer sites.
- Check reviews – don’t just look at the star rating – read the reviews whenever possible. It can give you a good idea of how well maintained the extension is.
- Look for the last updated date – while a plugin that hasn’t been updated in years isn’t inherently bad, you generally want to only use plugins that still receive regular updates.
- Don’t use nulled plugins – nulled plugins are often full of malware and backdoors. Don’t take the risk – just find a free alternative if you’re on a tight budget.
#Delete Unused Themes And Plugins
Even if you deactivate a theme or plugin, its files are still sitting around on your server, which means that malicious actors can still exploit them to access your site.
If you’re no longer using a plugin or theme and have no plans to reactivate it in the near future, delete it.
By following these principles, you can minimize the chance of any vulnerabilities because of your plugins or theme.
#4. Lock Down Your Logins With Strong Passwords And Technology
If a malicious actor gets access to your username and password, it doesn’t matter how secure the rest of your WordPress site is because they already have the keys to your front door.
It’s not just your WordPress admin account that’s potentially vulnerable, either – it’s also your hosting account and FTP account.
Here’s how you can keep all of your credentials secure so that hackers can’t just walk right in.
#Use Strong Passwords (And Make Other People Use Them, Too)
Despite all the highly-publicized security breaches lately, the two most common passwords are still:
123456Password
Don’t let that be you, especially with your Administrator account.
To help you pick a strong password, WordPress will automatically generate a secure password for you:
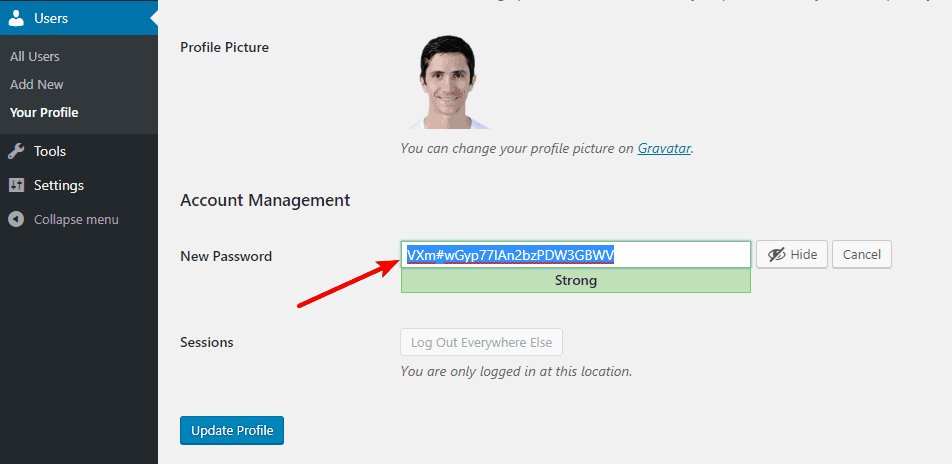
You can then securely store that password in a service like LastPass or KeePass.
Additionally, while WordPress no longer creates an “admin” username by default, you should still avoid choosing “admin” or “administrator” as your username.
Beyond your own account, if you allow registrations at your site, you want to make sure other people have secure passwords, too.
To force the issue, you can use the free Force Strong Passwords plugin (the Wordfence security plugin also includes this feature).
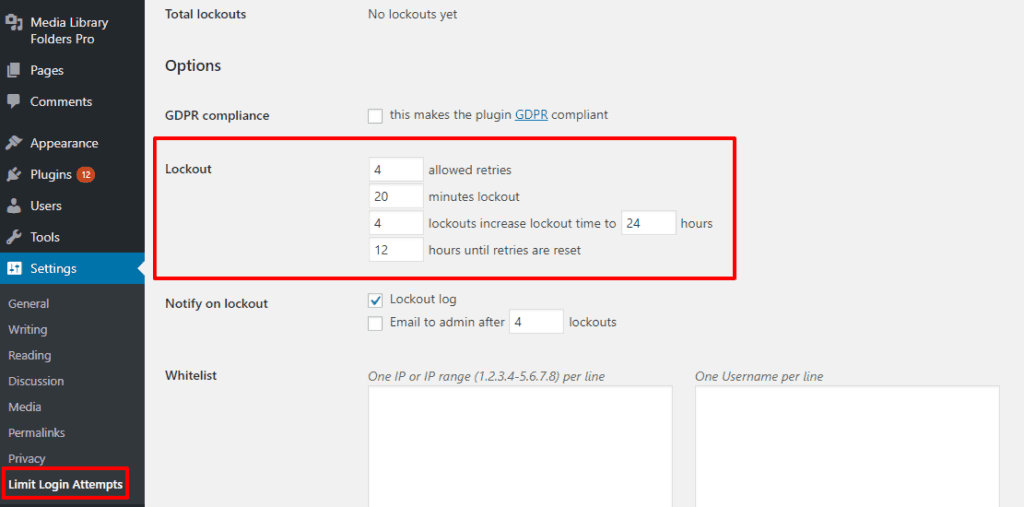
#Limit Login Attempts
If you use strong passwords, it will be exceedingly difficult for someone to guess your password. But, it’s still conceivable for someone to keep guessing and guessing and…guessing until they get it right. That’s called a brute force attack.
To completely eliminate the chance of someone brute forcing your password, you can limit the number of login attempts that a person can make (you’ll commonly see this approach at banks and other secure websites).
To set this up, you can use the free Limit Login Attempts Reloaded plugin (the Wordfence plugin also includes this feature):
#Use HTTPS For Secure Login
If you use HTTP on your WordPress site, a malicious actor can sniff out your password if you ever log in from a public Internet network (like working on your WordPress site at a cafe or airport).
To prevent this, and just generally create a more secure website, you should install an SSL certificate and use HTTPS. This ensures that all your site’s data is encrypted by default.
Most quality hosts, Presslabs included, offer free SSL certificates nowadays, so this shouldn’t cost you a dime.
#Consider Two-Factor Authentication
This one isn’t a necessity if you’ve implemented the other tips, but if you really want to put your logins on lockdown, you can add two-factor authentication.
With two-factor authentication, users need to enter both their password, as well as a one-time passcode (typically sent via a text or smartphone app).
Basically, unless malicious actors have access to both your password and your smartphone, they won’t be able to get in.
Two good options to add two-factor authentication to WordPress are Duo or Google Authenticator (Wordfence also has this feature).
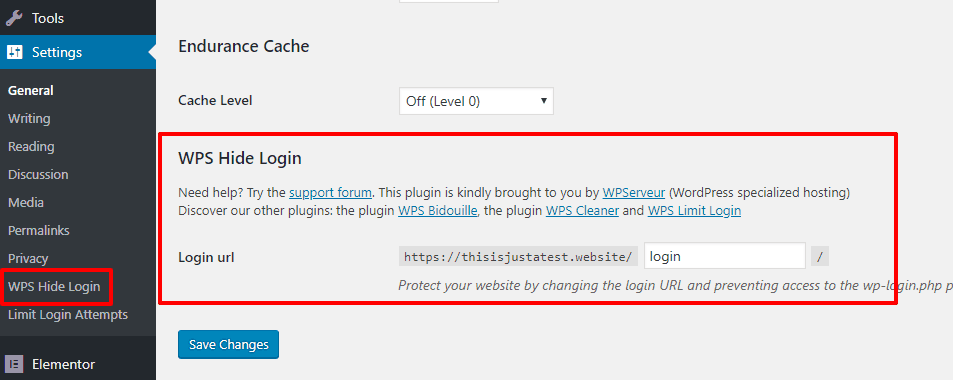
#Hide Your Login Page
If you implemented the tips above, hackers are unlikely to gain unauthorized access to your site. That is, you don’t need to hide your login page specifically for security reasons.
But even if it doesn’t move the needle much for security, it can still cut down on a ton of bot traffic to your wp-login.php, so it’s still worth doing for that reason alone.
The easiest way to hide your login page is via the free WPS Hide Login plugin (or Wordfence):
#5. Always Keep A Recent Backup Handy
Ok, keeping regular backups of your website doesn’t directly secure it. But it does mean that no matter what happens, you’ll always have a clean version of your site to restore if anything does manage to get through your defenses.
If you host at Presslabs, we have a multi-layered backup policy in place to automatically keep all your data safe.
If you host elsewhere, UpdraftPlus is a good free plugin that you can set up to run automatic backups on a set schedule.
#Five Other Smaller WordPress Security Tips
Implementing just the tips above should already make your site secure. But if you want to lock it down like Fort Knox, these five tips can beef up your security even further.
If you use a secure WordPress host, your host will likely have many of these configurations already in place. Likewise, a security plugin like Wordfence can also handle many of these for you.
If not, you’ll need to be handy with editing your site’s files via SFTP. Typically, you’ll make most of your tweaks by editing your site’s .htaccess and wp-config.php files.
#6. Don’t Allow File Editing Via WordPress Dashboard
By default, WordPress lets Administrators edit theme and plugin files right from the WordPress dashboard. That means if someone does get their hands on an admin account (which should now be very difficult!), they’ll be able to easily execute their own code without the need for any direct server access.
To block this type of file editing, you can add the following code snippet to your site’s wp-config.php file:
define('DISALLOW_FILE_EDIT', true);#7. Follow Principle Of Least Privilege To Restrict User Access
The Principle of Least Privilege is a common security protocol that basically says: only give users the minimum power required for them to perform their tasks.
On WordPress, that means understanding user roles and only giving other users at your site the lowest user role they need to perform their duties:
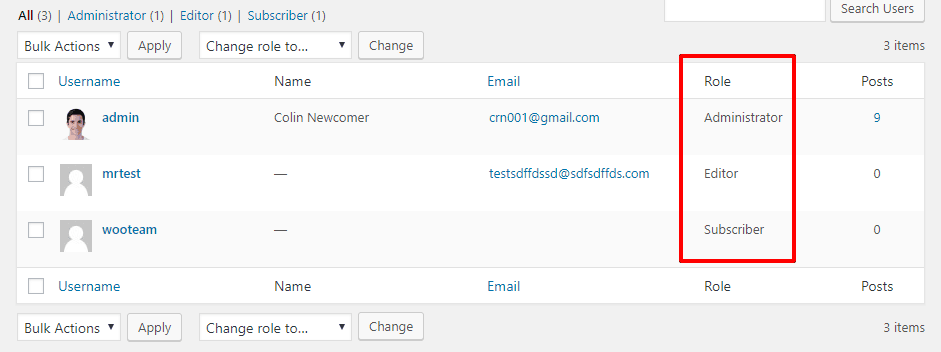
Unless you 100% trust a user, you should never give anyone else the Administrator user role. And if you allow third-party authors, you should give them either the Editor or Author roles, depending on how much power they need.
To understand what each default user role gives access to, consult the Capability vs. Role table at the WordPress Codex.
#8. Block File Execution In wp-content/uploads folder
A common strategy for hackers is to upload PHP files to your wp-content/uploads folders and then execute them to access your site.
To stop this from happening, you can add the following code snippet to the .htaccess file in your uploads folder:
<Files *.php>
deny from all
</Files>#9. Restrict Access To wp-config.php
Some people say you should flat out move your wp-config.php file to a different directory. There are arguments on both sides about whether or not this actually improves security.
According to the WordPress Codex, though, the best way to restrict access to wp-config.php is to add the following snippet to your .htaccess file:
<files wp-config.php>
order allow,deny
deny from all
</files>#10. Make Sure You Use Proper File Permissions
At Presslabs, we automatically implement proper file permissions for you to keep your site secure.
If you host elsewhere, you should read up on the ideal file permissions for WordPress and make sure you follow them.
As general rules:
- Most files should be 644 or 640, except for wp-config.php, which should be 440 or 400.
- Directories should be 755 or 750 (never 777).
#Let Presslabs Be Your WordPress Security Partner
WordPress security doesn’t have to be complex. If you implement the five big-ticket items from above, you’ll already have set yourself up with a secure WordPress site.
And if you want to lock it down even more, you can implement the smaller security tips.
Better yet, you don’t need to handle your site’s security by yourself. When you host with Presslabs, we can help you implement many of these practices:
| Technique | How Presslabs Handles It |
| Keep WordPress Updated | Easy staging environments to quickly test new updates before you apply them. |
| Secure wp-admin | Free SSL certificate to keep your data secure, as well as complete separation of your public site from the wp-admin area. |
| Backups | Multi-layered backup policy to keep your data safe. |
| Disable file editing | You can easily make this tweak yourself from the Presslabs dashboard. |
| Block PHP execution | This is automatically forbidden on Presslabs. |
| Restrict access to wp-config.php | At Presslabs, we block access to wp-config for security reasons. Most of the wp-config configurations are available either directly from the Presslabs dashboard, or by submitting a support request. |
| Use proper file permissions | Presslabs locks down files with proper permissions automatically. |